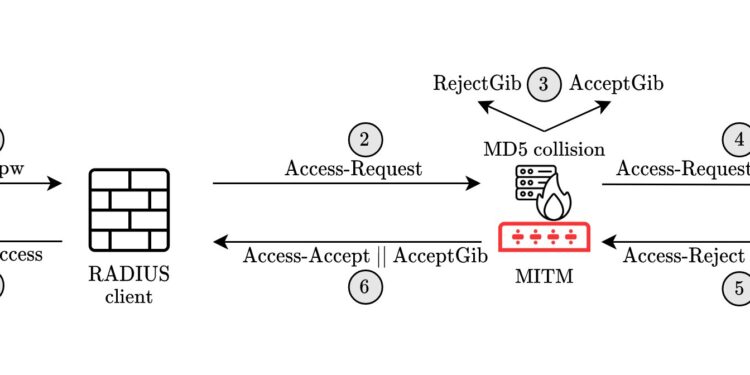
The Blast-RADIUS attack flow. More than 90 vendors participated in a coordinated disclosure and issued security bulletins. Credit: Goldberg et al.
A widely used security protocol that dates back to the days of dial-up Internet has vulnerabilities that could expose large numbers of networked devices to attack and allow an attacker to take control of traffic on an organization’s network.
A research team led by computer scientists at the University of California, San Diego, studied the Remote Authentication Dial-In User Service (RADIUS) protocol and discovered a vulnerability they called Blast-RADIUS that has existed for decades. Designed in 1991, RADIUS allows networked devices such as routers, switches, or mobile devices to use a remote server to validate login or other credentials.
This is a common configuration in enterprise and telecommunications networks because it allows credentials to be managed centrally. Therefore, RADIUS is a critical part of modern telecommunications and enterprise networks; in large enterprises, it can control access to tens of thousands of switches.
The authors of the study, “RADIUS/UDP Considered Harmful,” include researchers from Cloudfare, Centrum Wiskunde & Informatica, BastiionZero, and Microsoft Research. It was presented last week at the USENIX Security 2024 conference.
“This is one of the largest and most complex vulnerability disclosure processes we’ve ever encountered,” said Nadia Heninger, a professor in the Department of Computer Science and Engineering in the Jacobs School of Engineering. “Given the breadth of use of this protocol, it’s surprising that it hasn’t been the subject of any formal security analysis in the academic cryptography and security communities.”
Heninger notes the great divide between those who deploy these protocols and those who study them.
Researchers have discovered the ability for a “man-in-the-middle” attack on communication between a RADIUS client (or the victim’s network device) and a RADIUS server to forge a valid protocol accept message in response to a fake login or authentication request. This could give an attacker administrative access to network devices and services without having to guess or brute-force passwords.
According to the authors, the cause of this vulnerability is that RADIUS was developed before the design of a proper cryptographic protocol was well understood. It uses an authentication check based on an ad hoc and insecure construction based on the MD5 hash function, which has been known to be flawed for two decades.
However, the authors note that the RADIUS protocol was not updated when MD5 was broken in 2004. Prior to their work, the protocol standards maintainers defining RADIUS believed that the MD5-based construct used in RADIUS was still secure.
Vendors have released patches that implement the authors’ recommended short-term mitigations for this vulnerability. System administrators should check for patches for the protocols they use with RADIUS and apply the updated configuration options suggested by their vendors.
The authors disclosed their findings (security advisories CVE-2024-3596 and VU#456537) and over 90 vendors were involved in a coordinated disclosure and issued security bulletins.
The research team includes Heninger, Miro Haller, and Adam Suhl of UC San Diego; Sharon Goldberg of Cloudfare; Mike Milano of BastionZero; Dan Shumow of Microsoft Research; and Marc Stevens of Centrum Wiskunde & Informatica.
More information:
Article: RADIUS/UDP considered dangerous
Provided by University of California – San Diego
Quote: Computer scientists discover vulnerabilities in popular security protocol (2024, August 20) retrieved August 20, 2024 from
This document is subject to copyright. Apart from any fair dealing for the purpose of private study or research, no part may be reproduced without written permission. The content is provided for informational purposes only.